Using JSON Web Tokens (JWT)
You might be using JSON Web Tokens (JWT) as part of the authentication process in your API. In that case, there is a chance you need to encode or decode JWT token as part of your testing workflow. RapidAPI Testing allows you to perform this action right within your testing flow.
JWT Encode
We will first start with encoding a JWT. Let's walk through a simple example where you want to verify that your endpoint generates a JWT token.
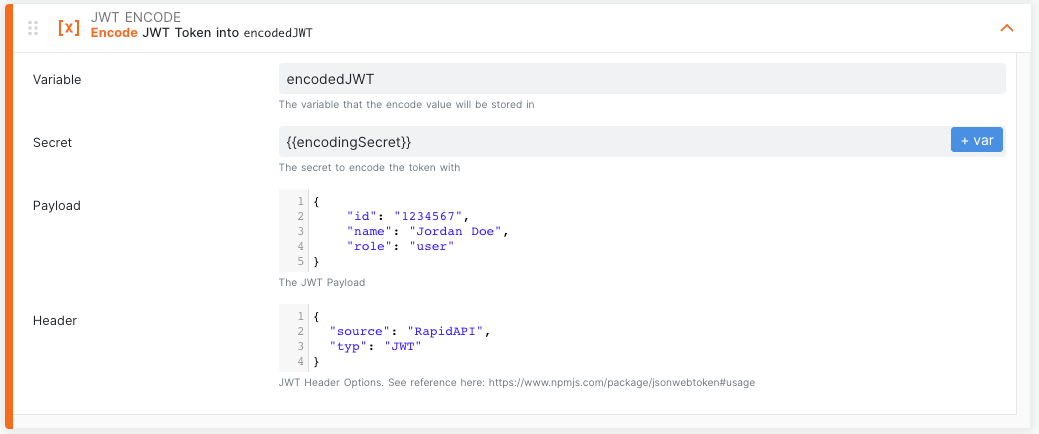
First, insert the JWT Encode step into your test. In this example, you will encode a sample user's information. The JWT Encode step is made up of four fields:
-
Variable is the name of the variable in which the resulting token is stored. In the example below, when subsequent steps need to use the token, we will access it through
encodedJWT. -
Secret is a private key value used to encode the JWT. In the example below, we are using a secret value saved in the variable
encodingSecret. -
Payload is the data you want to store in your JWT. In the example below, we are storing an ID, name, and role for a sample user named Jordan Doe.
-
Header is generally used to store the type of the token and the signing algorithm however you can customize this field as needed. In the example below, we are storing a key called "source" with a value of "RapidAPI". Note that this field is optional.
In subsequent steps, we can now use encodedJWT as a variable to access the token we just generated.
For more information, see the JSON Web Token NPM reference.
JWT Decode
We will use another simple example where we have a JWT token that we want to decode to verify the user information encoded in it.
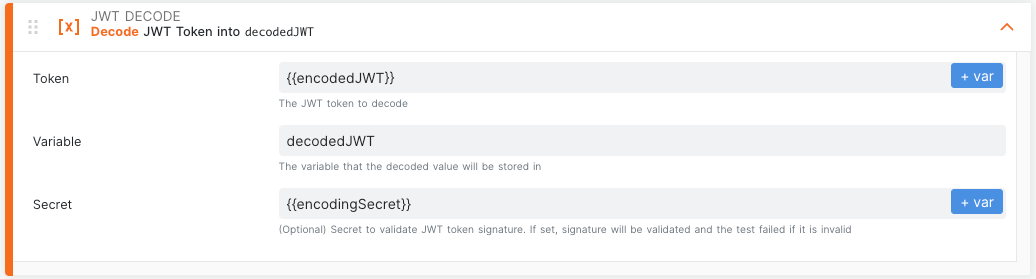
First, add the JWT Decode step to your test.
-
Enter the token you want to decode in the Token field.
-
Enter a named variable in the Variable field. This is how we will access the decoded information in subsequent test steps.
-
If you want the JWT signature validated as part of this step, you can provide the secret in the Secret field. Note that if the signature does not validate, this step will fail.
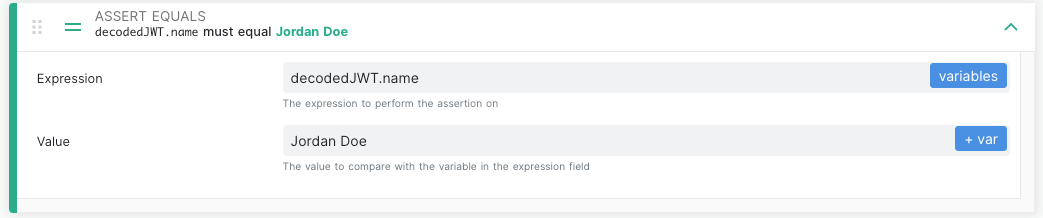
As a result of the above step, the decoded payload is now stored in the decodedJWT variable. Our next step may be to assert that the name encoded in the token was Jordan Doe. We can add an Assert Equals step, with decodedJWT.name as the Expressionand Jordan Doe as the Value.
Updated 5 months ago
